Inspiration
When I first saw it, it was extremely intriguing, but also slightly confusing.
On a website where people resell social media accounts with fancy usernames, I
came across a strange blog post online offering to create and then sell brand
new Microsoft email accounts with the @msn.com email domain name for $35 each.
It’s weird since, though Microsoft has gone through various versions of its
email service and has formerly offered domains including @live.com
@passport.com and @msn.com domains, currently, for years you’ve only been
able to create accounts with emails ending in @outlook.com and @hotmail.com.
But yet someone had discovered a method to create @msn.com-suffixed emails,
which was really strange. Did they work at Microsoft, or did they find a bug? As
soon as I saw the post, I got to work, scouring Google for more information
about the history of the domain. It wasn’t long before I struck success, and
figured it out for myself.
MSN Network

To start, I began by researching the history of the @msn.com domain a bit
further, thinking that perhaps some old tool associated with the domain would
have left an endpoint in existence to create emails with the antiquated domain.
It didn’t take long to learn that MSN stands for Microsoft network, which was
closely associated with a collection of eclectic Windows applications released
in 1995. At the time, various network services were offered at a low monthly
rate, and users could connect to the servers through Dial-Up. Around that time
was also when Microsoft released @msn.com email addresses for subscribers of
what they called “MSN premium subscriptions.” Though they later switched to
Hotmail and made it so that users without MSN premium could create Microsoft
email accounts for free, they never actually got rid of the old MSN premium
subscription. They’ve undergone various stages of rebranding for their email
services, but nevertheless, their program
Msn Premium still
exists, and is currently $9 a month, with the ability to get a full refund
before month end.
MSN Explorer

As I carefully read through the product’s description, things started looking
promising: they offer “computer wide security software, advanced phishing filter
technology, pop-up guard” but, most importantly, “multiple e-mail accounts.”
It wasn’t explicitly stated, but it seemed like those “multiple emails” were
likely to be somehow program-specific, and perhaps @msn.com-suffixed. Upon
finding the subscription page I eagerly purchased a month subscription, fully
intending to cancel right after exploration. I installed the program, which had,
of course, a pleasant built-in installer soundtrack, and was greeted by a
friendly, informative, archaic welcome screen and only slightly creepy “Hello,
Wolf” cortana voice. It took a bit of time, but eventually I found what I was
looking for. In the accounts tab of settings, under the “add user” form, in the
“create user” subform, I found an ancient Microsoft webpage meant for creating
@msn.com emails.
My first @msn

The form was a straightforward, requiring me to enter the desired email, along
with some additional information, such as birthdate, location, and name.
Interestingly, there was a “security question” field: a long-removed layer of
security that has since been replaced with two-factor authentication and
email/sms verification. Once I reached the end of the form, unlike the light
grey TOS checkboxes of the present day, I was required to type in my full name
to proceed. And then, it was there! A new email address had been created. After
a quick login on Microsoft’s normal log in page, I indeed had created a brand
new, 2023 @msn.com email. Of course, I wasn’t done yet; I decided to continue
tinkering.
Extracting the form
After more carefully inspecting the user flow, it occurred to me how truly
insecure the process was: the process lacked a captcha or verification of any
kind; it was a simple ASPX (predecessor to PHP!) form. So, what’s to stop
someone like me from creating a script to automate the process, and generate
thousands of accounts automatically? Apparently nothing, and so I tried doing
just that, as a proof-of-concept. I carefully inspected the form, looking for
ways to extract the endpoint of the form requests. Something that I noticed in
was that, for the brief loading gaps between pages of the form, a link flashed
at the top of the email creation widget. With a timely screenshot I was able to
extract the link, and with a long night of scouring and reverse engineering
network requests, I was able to write a script to reverse the process. Though
each paying @msn.com user was allowed to create 10 sub-user accounts, I
quickly figured out that detaching the sub-users from the main paying account
was meaningless, since the accounts were automatically ported to brand new
Microsoft accounts anyway. I was quickly able to make a tool to extract and
parse the HTML, make appropriate HTTP requests, and then load up a json with 1k
accounts. The process was seamless, and the brand new accounts were fully usable
with a working email, onedrive, and all.
Reporting the exploit
This was my first time discovering a website vulnerability, so I wasn’t quite sure how to proceed. I knew something had to be done, because it was evident that if anyone else with more computational and network power than I were to come along they’d be able to create hundreds of thousands of accounts automatically, which they could use easily use for scamming or email spamming. After a bit of Googling, I came across the Microsoft Security Response Center vulnerability report form, and wrote up a report along with a simple proof-of-concept script and video showcase. It took a while, but a few months later Microsoft was able to reproduce the bug, and a month after that they resolved the issue by adding a simple captcha to the form, which is still in place to this day. It’s just a simple text-captcha that can likely be solved with simple OCR, but I suppose it’s better than nothing.
The names

One thing I quickly learned through this process was how truly archaic
@msn.com email addresses really are. I quickly realized that, as an inevitable
result of there being no longer easily available, there were many unclaimed
emails with modern English words and topics. I began claiming emails like
covid@msn.com, airpod@msn.com, JoeBiden@msn.com, technophile@msn.com,
ethereum@msn.com, spotify@msn.com, and more. Since I was, at the time,
waiting for the captcha bypass vulnerability to get patched, I decided to write
a script for fun to automatically snag most of the Pokemon, and a bunch of
modern youtube channel names. I also figured out that one easy and effective way
to check if an @msn.com email exists is to simply use the default account
recovery form, wherein it only provides you a continue-confirmation if the
account exists, and tells you that the account doesn’t exist (and thus can be
taken) otherwise.
Make your own @msn email
As of recently…
As is stands now, @msn.com emails are still acquirable through the method
outlined above, but because of my report to MSRC there is now a captcha in
place. I imagine that as long as MSN Premium remains available, @msn.com
emails will remain available with it. Since Microsoft has a reputation for
supporting antiquated projects for long amounts of time, I anticipate that this
technique will work for a long time to come.
The steps
Disclaimer: Multiple people have emailed me now telling me that this no longer works, and it seems like Microsoft disabled creating @msn.com emails all together.
Here’s a straightforward list of the steps you can take to create an @msn.com
email account in 2023 and beyond. If you have any questions, feel free to
contact me.
-
Go to the msn premium purchase page and purchase 1 month of msn premium (~$10). As noted previously, you’ll be able to cancel this later for a full refund.
-
Visit membercenter.msn.com/signin.aspx, the member center sign in page on their website.
-
Click “Sign In,” and sign in with the same Microsoft you just purchased msn premium on.
-
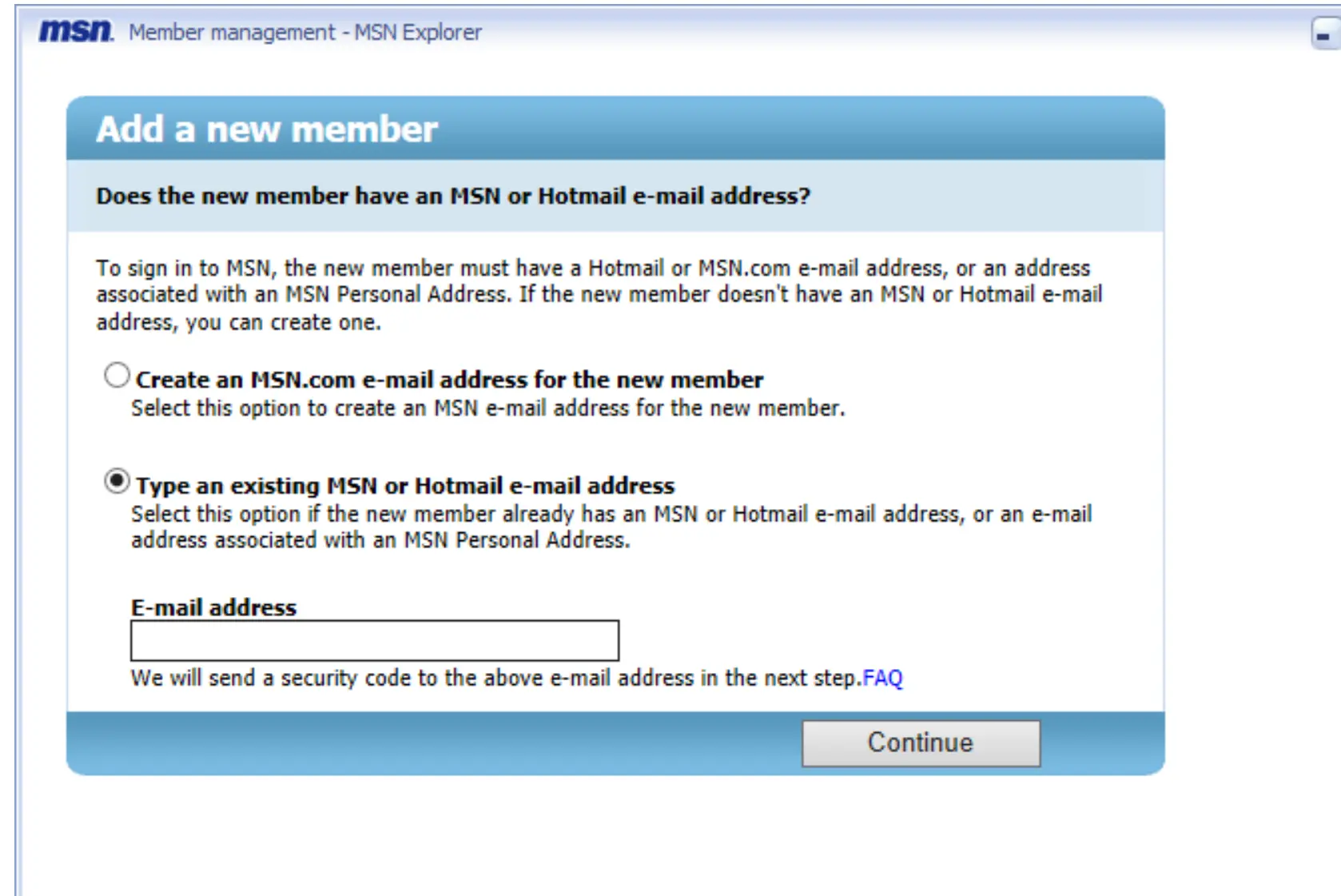
Visit texreg2.msn.com/wbum/Selector.aspx. This is the specific link that is embedded into Msn Explorer, and lets you add emails.
-
Click “Add a member,” and fill out the form that follows. The information is arbitrary, but make sure to save everything. After that, click next. You will have to complete a captcha as part of this process. Note that clicking enter after filling out the captcha box will reset it, so you need to manually click on the submit button.
-
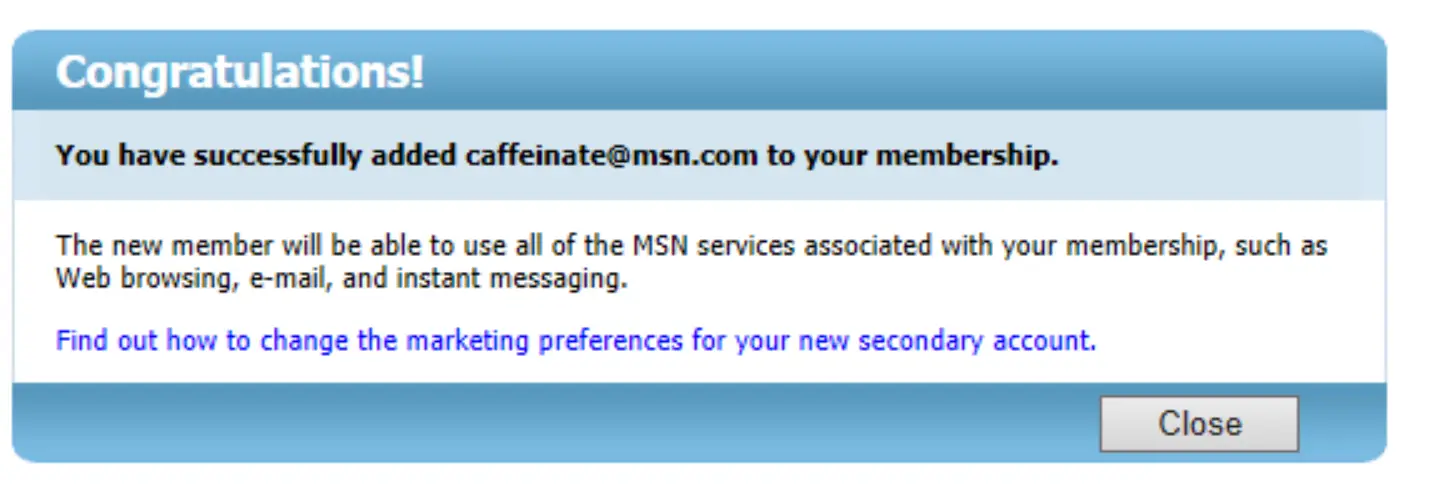
Enter the same name you entered prior in the name signature box and then click “Accept.” If a few seconds later it says “You have successfully added <email> to your membership” everything was done correctly.
-
Go to login.live.com and sign in to the account as normal.
-
Enter the new email you created for the email and click “Next.”
-
Your account should be successfully created and operational!